A vulnerability is defined in the ISO 27002 standard as “A weakness of an asset or group of assets that can be exploited by one or more threats” Vulnerability management is the process in which vulnerabilities in an organisation Digital Assets are identified and the risks of these vulnerabilities are evaluated. This evaluation leads to correcting (Remediation) the vulnerabilities and removing the risk or a formal risk acceptance by the management of the organization.
Why Vulnerability Management is important?
The increasing growth of cyber-crime and the associated risks are forcing most organizations to focus more attention on information security. Consequently, a vulnerability management process should be part of an organization’s effort to control information security risks.
This process will allow an organization to obtain a continuous overview of vulnerabilities in their Digital environment and the risks associated with them. Only by identifying and mitigating vulnerabilities in the Digital environment can an organization prevent attackers from penetrating their networks and stealing sensitive data and commercial information.
What makes an effective Vulnerability Management?
Context and risk weighting are key to effective vulnerability management. Weeding out false positives from the huge noise of vulnerability data is very, very important. We need to focus on what matters: patching all vulnerabilities is an unrealistic target, and a low false positive rate is essential to allow for high and critical issues being addressed.
Context is also an important component of how these issues are prioritised and why all organisations need to have a cyber risk management strategy in place. The idea of saying one vulnerability management solution is better than another because it ‘reports more issues’ is folly. We need to report on the items that matter.
Automation alone, ‘software testing software’, will never truly work – there will always be the need for human expertise to validate the software’s output. We are trying to defend systems from determined, highly expert humans, who in many cases have sophisticated automation tools at their disposal. For this reason, humans’ ability to understand context will never become obsolete. The most effective solution is the one that augments human capabilities using technology, as opposed to one that aims for 100% automation.
Prioritising the right vulnerability
Fortunately, there is good news in general for defenders, with most experts advocating a risk-based approach to vulnerability management as the holy grail. This approach means you reduce the sheer volume down to a more manageable ‘patch it now’ because it has a direct risk impact to your business’ list of vulnerabilities.
Using threat intelligence, the real world view of how specific vulnerabilities are being used and targeted by threat actors, as well as understanding the business risk appetite, including which physical servers or machines are the most critical – and which are exposed directly on the internet – allows you to shrink that volume of findings down to between 5% and 10% of the total. Thus, it means vulnerability management becomes more manageable and allows the defenders to ask the question: ‘Do I really need to worry right now about this vulnerability?
Who Needs a Vulnerability Management Program?
The simple answer is anyone who has assets connected to the Internet. Many industries require them in order to be compliant with regulations. Attacks resulting in data loss are often caused by breaches using known, unpatched vulnerabilities. If you have any asset on your network that is not patched regularly, a vulnerability management program is for you. In summary, a Vulnerability management process is comprised of the following activities:
- Identifying / tracking assets (build asset inventory)
- Categorizing assets into groups
- Scanning assets for known vulnerabilities
- Ranking risks
- Patch management
- Test patches & Apply patches
- Follow-up remediation scan – confirms vulnerability addressed.
Why it Matters
If your Vulnerability Management program isn’t working, take note of the following possible reasons:
- The huge volume of data collected from scanning is un-manageable – Note that focusing on collecting huge volume of data is the wrong approach.
- You are trying to eliminate all vulnerabilities – Note that this is inefficient and impossible
- You perform vulnerability scanning too often – This is also an inefficient paradigm, for example if the output quality is poor and volume is high, effectiveness is reduced.
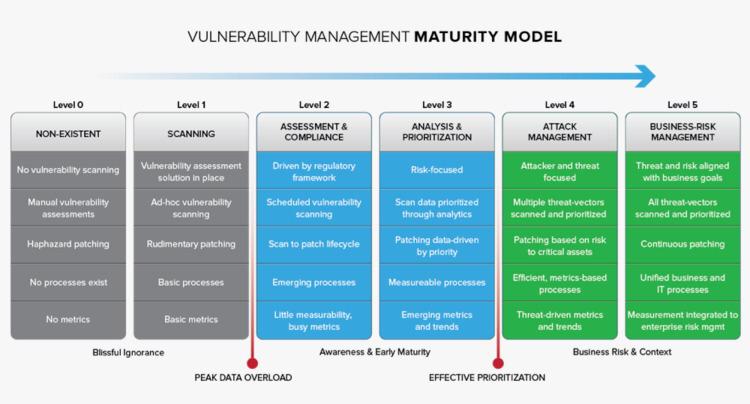
How Mature is Your Vulnerability Management Process?
The Vulnerability maturity model below should be used to outline what your company is doing, and what it should be doing. Of course, each company is different, and the path to reducing risk is never a straight line. It is, however, something that needs to be approached strategically, and taken seriously.
Growing Up: A Roadmap to Vulnerability Management Maturity – You should place a strong focus on identifying where your company’s security posture is in terms of vulnerability maturity. The vulnerability management maturity model shown above illustrates the scalability of a typical vulnerability management program.
Worth noting:
Upcoming Training on Risk & Vulnerability Management
How vulnerabilities are discovered, disclosed and dispatched makes a significant difference to risk management. And new research says we’re getting it wrong. This is the reason why Delta3 International is organising the following Instructor-Led online training for all organisation in Africa to attend:
- Internal Controls & Risk Management – 13 April
- Conducting Fraud Investigation – 20 April
- T Security Risk Management – 27 April
- Workplace Ethics Training – 25 May
In conclusions
Without a vulnerability management process in place, the management of an organization is blind to risks related to the security of the IT infrastructure. Implementing a vulnerability management process is all about managing risk. By having a well-defined process in place, an organization can obtain a continuous view of the risk associated with the presence of security vulnerabilities in its IT systems.
This allows management to take well-advised decisions with regards to remediating actions that could be implemented to reduce the risks. In short, any organization that wants to obtain an understanding of the security risks they are facing due to the technology they are using should implement a vulnerability management process
However, introducing a new vulnerability management process within an organization can also be challenging. In order to ensure a successful vulnerability management program, attention should be paid to a number of aspects. First of all, roles and responsibilities should be clearly assigned. Ensure all stakeholders within the organization know what to expect. Then select a vulnerability scanning technology that suits the needs of your organization. Sufficient attention should be paid to the configuration and fine tuning of the vulnerability scanner technology.
Finally, when starting out with vulnerability management, it is recommended to limit the scope of the initial vulnerability scans. This prevents initial scans that result in tens of thousands of vulnerabilities. A better approach would be to only select a limited set of vulnerabilities (such as the SANS TOP 10) or only those that are marked as “high risk” by the vulnerability scanner tool.
We at Delta3 International stands ready to work with your organisation to help start / scale an appropriate vulnerability management program that meets the specific need of your organisation.
>>>The writer is a UK based InfoSec & Business Continuity Consultant, with main focus on helping organisations to implement Digital Transformation, defend their digital infrastructure and plan their Business Continuity Strategies. Del is also a Freelance writer, international Conference speaker and a Global trainer. Contact: [email protected] | WhatsApp:+44 7973 623 624 | Web: www.delta3.co










