InfoSec Advisory with Del Aden
Organisations worldwide have moved to remote work scenarios in response to the COVID-19 pandemic…. However, moving to a remote workforce has presented I.T. and InfoSec teams with key challenges surrounding the traditional perimeter security model.
Further, the move to the Cloud presents an additional threat vector that must be well understood with respect to data security.
As you know, Cloud-based services and mobile computing have changed the technology landscape for modern enterprises. Today’s workforce often requires access to applications and resources outside traditional corporate network boundaries, rendering security architectures that rely on firewalls and virtual private networks (VPNs) insufficient. Consequently, Changes brought about by Cloud migration and a more mobile workforce have led to the development of an access architecture called Zero Trust.
But what is Zero Trust?
Zero Trust access architecture addresses the modern security challenges that come with Cloud migration and a mobile workforce. By implementing Zero Trust, an organisation takes a layered approach to secure corporate and customer data. A typical phased implementation of Zero Trust centres on strong user identity, device health verification, validation of application health, and secure, least-privilege access to corporate resources and services.
The Need for Zero Trust model
Perimeter security model (traditional) is being replaced by Zero Trust model – WHY?
► Perimeter security model (traditional) makes assumptions that everything (and everyone) inside the perimeter can be reasonably protected, if not completely trusted (insider threat scenarios)
► However, as Cloud-based workplaces (and remote work) become the new normal, the perimeter security model gets broken fast – especially in hybrid Cloud application environments, and Zero Trust Model is becoming the new security approach
► In Zero Trust Model, the infrastructure is untrusted, the data is protected, the users are identified and known. Thus, eliminating the assumption of baseline infrastructure protection—a mind-set versus a technology
► Implementing a Zero Trust model involves strategic thinking to build an overall Identity-focused programme.
And the new reality…
Based on the principle of ‘never trust, always verify’, Zero Trust helps secure corporate resources by eliminating unknown and unmanaged devices and limiting lateral movement. Implementing a true Zero Trust model requires that all components—user identity, device, network and applications—be validated and proven trustworthy. Zero Trust verifies identity and device health prior to granting access to corporate resources.
When access is granted, applying the principle of least privilege limits user access to only those resources that are explicitly authorised for each user; thus reducing the risk of lateral movement within the environment.
In an ideal Zero Trust environment, the following four elements are necessary:
- Strong identity authentication everywhere (user verification via authentication)
- Devices are enrolled in device management and their health is validated
- Least-privilege user rights (access is limited to only what is needed)
- The health of services is verified (future goal)
Typically, Zero Trust establishes a strict boundary of trust around corporate and customer data. For end users, Zero Trust delivers a simplified user experience that allows them to easily manage and find their content. And for customers, Zero Trust creates a unified access platform that they can use to enhance the overall security of their entire ecosystem.
Zero trust scenarios
We have identified four core scenarios to achieve Zero Trust. These scenarios satisfy the requirements for strong identity, enrolment in device management and device health validation, alternative access for unmanaged devices, and validation of application health. The core scenarios are described here:
Scenario 1: Employees can enrol their devices into device management to gain access to company resources.
Scenario 2: I.T./InfoSec can enforce device health checks per application or service.
Scenario 3: Employees and business guests have a secure way to access corporate resources when not using a managed device.
Scenario 4: Employees have user interface options (portal, desktop apps) that provide the ability to discover and launch the applications and resources they need.
How best to implement Zero Trust?
If you are thinking of implementing a Zero Trust access architecture, it is advisable to take a structured approach toward Zero Trust that will span many years. The diagram below illustrates a roadmap, organised by phase, that includes an overview of milestones, goals, and current status. The process emphasises identity-driven security solutions and centres on securing user identity with strong authentication as well as the elimination of passwords, the verification of device health, and secure access to corporate resources.
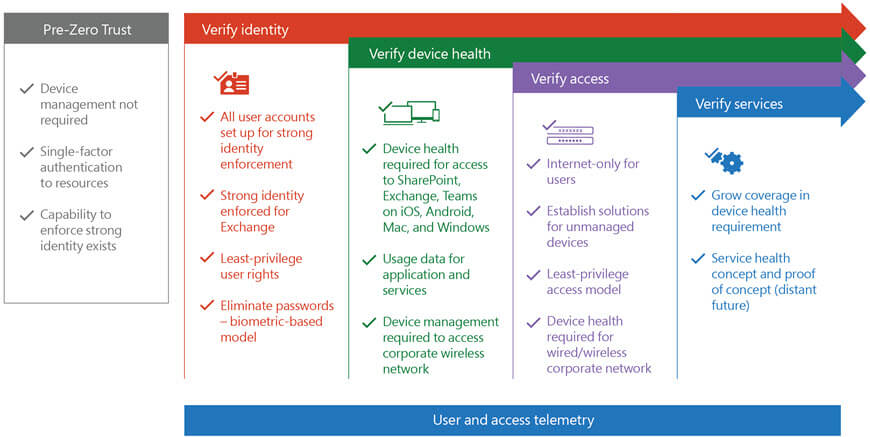
Source: Microsoft – The major components of work performed in each phase of Zero Trust.
Why Financial data security is important
Financial Data security is one of the most daunting tasks for IT and infosec professionals. Each year, companies of all sizes spend a sizable portion of their IT security budgets protecting their organisations from hackers intent on gaining access to their financial data through brute force, exploiting vulnerabilities or social engineering.
High-profile companies such as Capital One, Evite and Zynga experienced data breaches that exposed more than 100 million customer accounts each.
The lessons from these breaches are numerous, including the need to do the following:
- Review credential requirements and policies;
- Keep track of what data is retained and where it is stored;
- Check for Cloud misconfigurations regularly
- Provide the requisite training to all staff and employees- an example of such training can be found here
In conclusion, Define your boundaries of trust…

In conclusion, as security breaches persist most organisations understand that something must be done, and Zero Trust is most certainly worth looking into.
However, Choosing the right security partner that understands the Zero Trust Model is equally highly desirable. Discover security with Delta3 International – Speak to our security team today or request a call back via our WhatsApp line +233 234 160 272
Support Information Security in Africa by sponsoring this Weekly Article and promote your Brand
>>>Del Aden is a UK-based Enterprise Architect and Information Security Consultant. He is experienced in executive consulting, architecture, and assessment work across the globe and in a wide variety of industries, including finance, insurance, healthcare, education, the intelligence community, retail, and government. He also has expertise in building & running security programmes, Security Strategy Assessment & Consulting, Cyber Practitioner, Business Continuity and strategic consulting. An astute speaker and trainer and a technology journalist. Contact author:[email protected] | WhatsApp:+44 7973 623 624 | Web: www.delta3.co










