As you may have read, last couple of weeks, the FBI sent out an alert warning of four new DDoS attack vectors, three of which have already been exploited and resulted in several large DDoS attacks across the globe. DDoS attacks have increased by 500% as a result of Covid-19, and 2020 is shaping up to be a record-breaking year for cyber-attacks.
But what is a DDoS attack?
A distributed denial of service attack (hence the abbreviation DDoS) is an attack intended to make a service unavailable and prevent the legitimate requests to the system. Typically, a distributed denial of service (DDoS) attack is an attempt to take a website offline by overwhelming it with internet traffic.
It may be:
- Flooding of a network to prevent its operation – in this case, hackers overflow a network server or web server with frequent request of services to damage the network.
- Disruption of connections between two machines, thereby preventing access to a particular service
- Obstruction of Access to a service to a particular person.
The denial of service attack can block a file server, making it impossible to access a web server or prevent the distribution of mail in a company. In a DDoS attack, a large number of requests are sent simultaneously from multiple points of the Net. The intensity of this “cross fire” makes Service unstable, or worse, unavailable.
A DDoS (Distributed DoS) attack’s target is to render a server, a service or infrastructure unavailable by overloading the bandwidth of the server, or by monopolizing resources until exhaustion.
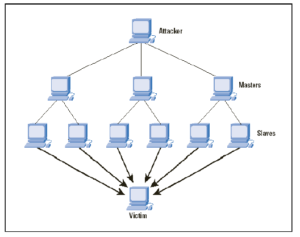
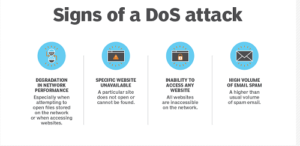
DDoS attack techniques have continually evolved over the last several years.
For example, 2013 was the year of NTP (Network Time Protocol) amplification. In 2014, it was SSDP (Simple Service Discovery Protocol) attacks. And in 2016, we saw the Mirai botnet and attacks from IoT devices.
As such it is not at all surprising to learn of a new attack technique in 2020…
Two weeks ago, the FBI sent out an alert warning of four new DDoS attack vectors that have been identified. Of these, three have already been exploited, resulting in several large DDoS (Distributed Denial of Service) attacks across the globe.
The four new vectors are:
- Constrained Application Protocol (CoAP)
- Web Services Dynamic Discovery (WS-DD)
- Apple Remote Management Service (ARMS)
- Jenkins open source automation server
According to the FBI, these new vectors present a heightened threat as they are essential network protocols, and therefore unlikely to be removed by device makers.
How does a DDoS attack happen?
To carry out a DDoS attack, cybercriminals often gain control of a network of devices (botnets) and use them to direct a surge of traffic to your servers. Their aim is to overwhelm your systems with requests for access, resulting in downtime for your business. Because the access requests come from real devices it can be difficult to filter the fake traffic from legitimate requests, leaving your systems unprotected without the right security precautions in place.
Different DDoS attack vectors target different layers of a network connection – meaning there are various types of this kind of attack. The motivations of an attacker can also be varied – it can be political, an attempt to gain competitive advantage, or designed to cause a distraction while carrying out a data breach elsewhere on your system.
An ever-growing threat
Nowadays, Attackers are increasingly targeting Cloud Service Providers (CSPs) because they are a form of critical infrastructure. According to Lawrence Orans, vice president analyst at Gartner. “A successful DDoS attack against a major CSP could be highly disruptive to businesses and consumers that traverse the CSP’s network.”
However, the discovery of these new vulnerabilities serves as a reminder to remain vigilant against even the most common of cyber-threats. Whilst 2020 has been far from average (in many ways), cybercrime has surged, demonstrating that attackers will seek out and exploit any vulnerability – whether it’s the result of a network weak spot or a global pandemic.
In fact, reports show that DDoS attacks have increased by 500% as a result of the Covid-19 situation. As such organisations in Africa should understand that threats such as DDoS attacks continually evolve and develops their protection to mitigate new risks.
DDoS prevention Best Practice
As cyber attackers become more resourceful, DDoS attacks will continue to evolve, as such this is not something that organisations and service providers can simply brush off. While there’s nothing many organisations can do to discourage attackers, however they should update their defense strategy and focus on enhancing their network security posture to ensure their services are not affected.
For any business, downtime is catastrophic. You need your systems to be accessible, even in the midst of a DDoS attack. As such you need to deploy solutions that are designed to mitigate even the most sophisticated of attacks. Organisations have to look for ways in which they can much more effectively manage the DDoS attacks, so that their infrastructure and their customers do not suffer any damage.
In conclusion, stay secure in 2020 and beyond
With 2020 shaping up to be a record-breaking year for cybercrime, it’s more important than ever that your business is prepared for anything and protected against the latest threats. With cyber-attack capabilities increasing and cybercriminals’ motives rapidly reacting to global events, remaining vigilant to DDoS attacks is paramount to business survival this year and beyond.
Investing in DDoS protection as part of your cybersecurity strategy ensures your business is protected from downtime at the hands of unexpected threats. Choosing the right security partner that understands the threats such as DDoS attacks is highly desirable
Discover security with Delta3 International – It’s our mission to make sure your business is as secure as possible, whatever new threats arise. Speak to our security team today or request a call back via our WhatsApp line +233 234 160 272.
Support Information Security in Africa by sponsoring this Weekly Article and promote your Brand
About the Author
As an Enterprise Architect and Information Security Consultant, Del Aden is an industry-recognized security expert with over 20 years of hands-on experience in consulting, training, public speaking, and expert witness testimony. As the Managing Partner for Delta3 International, Del now focuses on helping customers prevent security breaches, detect network intrusions, and respond to advanced threats.
An astitute speaker and trainer, Del is on the cutting edge of cybersecurity research and development. For comments, contact author: [email protected] Phone / WhatsApp:+44 7973 623 624. Website: www.delta3.co










