By Daniel Kwaku Ntiamoah ADDAI
Cyber-attacks are an ever-present threat that no organization can afford to ignore. Ghana, like many other nations, has seen a significant rise in cybercrime, impacting businesses of all sizes and individuals at large. The Cybersecurity Authority reports a staggering GH¢49.5 million in financial losses through cybercrime in the first half of 2023 alone, underscoring the growing menace faced by local businesses.
Globally, cybercrime continues to escalate at an alarming rate. Global Cybersecurity firm Sophos reports a surge in ransomware payments by an unprecedented 500% in 2023, with demands averaging over US$1 million per attack. This surge has affected organizations across industries, highlighting the critical need for robust cybersecurity measures.
It’s not a matter of if, but when, the next cyber-attack will strike. For Ghanaian companies, the stakes are particularly high. A successful attack can disrupt operations, erode customer trust, and result in substantial financial losses. In 2022, cyber-attacks cost Ghanaian businesses an estimated US$105 million, emphasizing the urgent need for proactive defence strategies.
Consider the devastating impact of a ransomware attack that recently crippled major financial institutions and other critical infrastructure firms in Accra, locking up critical data and demanding a hefty ransom. Or the phishing schemes that have duped countless employees into revealing sensitive information, leading to severe data breaches. These incidents are not isolated; they are part of a larger trend that threatens the very foundation of our digital infrastructure.
This article highlights essential hardening techniques that can help companies prepare for the inevitable cyber-attacks. By proactively enhancing their security measures, businesses can build resilience and safeguard their future. We will delve into strategies that will fortify your defences and ensure you’re ready for the next wave of cyber threats. Whether you’re a small startup or a large enterprise, these steps will help you protect your valuable assets.
Assessing your current security posture
Understanding your organization’s current security posture is foundational to effective defence. Each additional layer of security contributes significantly to achieving a robust defence-in-depth strategy. Evaluating and assessing your organization’s security posture is critical to pre-empting potential breaches and mitigating risks effectively.
Vulnerability assessment
Identifying and addressing vulnerabilities proactively is foundational to robust cybersecurity. Regular vulnerability assessments leverage tools like Nessus, OpenVAS, and Qualys to scan systems comprehensively. These assessments provide detailed insights into potential weaknesses, enabling organizations to prioritize and implement timely security patches and updates.
Risk assessment
Understanding the specific risks facing your organization is essential for targeted cybersecurity efforts. By evaluating risks based on potential impact and likelihood, organizations can allocate resources effectively to mitigate these threats. Comprehensive risk assessment frameworks such as NIST SP 800-30 or ISO 31000 guide organizations in identifying, assessing, and managing risks across their operations.
Compliance and audit
Adhering to regulatory requirements and industry standards is crucial for maintaining a secure environment. Regulations such as Cybersecurity Act, Bank of Ghana’s Cyber/Information security directive, GDPR and PCI DSS set forth stringent guidelines for data protection and cybersecurity practices. Regular security audits not only ensure compliance but also verify the effectiveness of implemented security controls. These audits provide organizations with insights into potential gaps in their security posture and opportunities for improvement.
Penetration testing
Simulating real-world cyber-attacks through penetration testing helps organizations assess the effectiveness of their security defences. By identifying vulnerabilities that automated scans may miss, penetration tests, including black-box, white-box, and grey-box tests, provide valuable insights into the resilience of systems and networks. These tests enable organizations to proactively address weaknesses and enhance their overall cybersecurity posture.
Hardening techniques
Implementing robust hardening techniques is crucial for fortifying your organization’s cybersecurity defences. This section provides comprehensive details on each technique, enhancing understanding and application.
Removing unneeded services
Removing unneeded services reduces the attack surface by eliminating unnecessary software components that could introduce vulnerabilities. Services that are not essential for business operations should be disabled or removed to minimize potential entry points for attackers. How?
- Conduct regular audits to identify and remove services that are no longer required.
- You can use basic tools like netstat, tasklist, or sysinternals to identify running services and their associated ports.
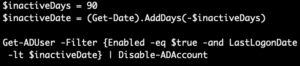
Disabling unused accounts
Disabling unused accounts prevents unauthorized access by ensuring that only active accounts are accessible. Dormant accounts, such as those belonging to former employees or unused administrator accounts, pose a significant security risk if not properly managed. How?
- Implement automated processes to disable accounts promptly after employees leave the organization.
- Use identity and access management (IAM) solutions to enforce least privilege access which is a major tenant in the Zero-Trust Framework.
Images/templates hardening
Hardening images and templates involve configuring base operating system (OS) and application images with secure settings before deployment. This ensures that all new instances inherit these secure configurations, maintaining consistency and reducing manual configuration errors. How?
- Use configuration management tools like Ansible, Chef, or Puppet to automate image hardening processes.
- Implement CIS benchmarks or vendor-specific hardening guidelines for OS and application images.
Removing end-of-life devices
End-of-life devices refer to hardware that is no longer supported by the vendor with security updates or patches. These devices are susceptible to known vulnerabilities that can be exploited by attackers. How?
- Develop a device lifecycle management policy to identify and retire end-of-life devices promptly.
- Consider hardware refresh cycles to ensure devices are regularly upgraded to supported versions.
Removing end-of-support devices
Like end-of-life devices, end-of-support devices are those for which the vendor no longer provides technical support, including security updates. Continuing to use these devices exposes the organization to potential security breaches. How?
- Conduct a risk assessment to prioritize the removal of end-of-support devices based on criticality and potential impact. Your asset (hardware, software) inventory is the best place to start from.
- Explore alternative solutions such as virtualization or cloud migration for unsupported hardware.
Local drive encryption
Encrypting local drives protects sensitive data stored on devices from unauthorized access. In the event of physical theft or loss, encrypted data remains inaccessible without the decryption key, maintaining confidentiality. How?
- Implement full disk encryption (FDE) solutions such as BitLocker (Windows) or FileVault (macOS).
- Ensure encryption keys are stored securely and managed effectively to prevent unauthorized access.
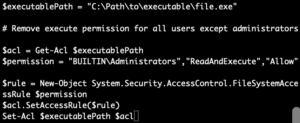
Enable NX/XN Bit and Implement File Read-Write-Execute Controls
Enable NX/XN Bit: Enabling the NX (No Execute) or XN (Execute Never) bit in hardware and operating systems helps prevent buffer overflow and other memory-based attacks by marking certain memory regions as non-executable. This mitigation technique ensures that memory pages intended for data cannot be executed as code, thereby thwarting many common exploit techniques.
Implement File Read-Write-Execute Controls: Controlling file permissions for read, write, and execute operations is crucial for limiting the impact of potential security breaches. By enforcing strict controls over file permissions, organizations can prevent unauthorized execution of malicious scripts or binaries, reducing the risk of compromise. How?
Enable NX/XN Bit:
- Verify hardware support for NX/XN bit functionality in CPUs and enable it in BIOS settings.
- Configure operating systems to support NX/XN bit enforcement for executable memory.
- Regularly audit and update NX/XN bit configurations to maintain effective protection against evolving memory-based attacks.
Implement File Read-Write-Execute Controls:
- Use access control lists (ACLs) or file system permissions to restrict file execution privileges based on user roles.
- Implement file integrity monitoring (FIM) solutions to detect unauthorized changes to executable files.
Secure encrypted enclaves/memory encryption
Secure encrypted enclaves or memory encryption enhances data protection by encrypting sensitive information at the hardware level. This ensures that even if an attacker gains access to memory, encrypted data remains unreadable without the decryption key. How?
- Implement hardware-based encryption technologies such as Intel SGX or AMD SEV for secure enclaves.
- Use advanced memory encryption solutions to protect data at rest and in transit within the memory.
Shell restrictions
Shell restrictions limit the capabilities and commands accessible through command-line interfaces (CLI), reducing the risk of privilege escalation and unauthorized system modifications. How?
- Utilize tools like SELinux or AppArmor to enforce mandatory access controls (MAC) and restrict shell capabilities.
- Implement role-based access controls (RBAC) to limit users’ ability to execute privileged commands.
Address Space Layout Randomization (ASLR)
ASLR randomizes the memory addresses used by system processes, making it difficult for attackers to predict the location of executable code and execute successful memory-based attacks. How?
- Enable ASLR in operating systems and applications to enhance resilience against buffer overflow and similar attacks.
- Regularly audit and update ASLR configurations to maintain effectiveness against evolving attack techniques.
Incident response planning as preparation for cyber attacks
Effective incident response planning is essential for preparing organizations to handle cyber-attacks swiftly and effectively. Establishing a multidisciplinary incident response team (IRT) with defined roles and responsibilities is the first step in preparation. Regular training and simulation exercises ensure the team is ready to act immediately when an incident occurs. Developing detailed incident response policies and procedures, aligned with industry standards and regulatory requirements, provides a structured approach to managing incidents.
Proactive detection and analysis using tools such as security information and event management (SIEM) systems, intrusion detection and prevention systems (IDPS), and automated threat intelligence feeds enable real-time identification and assessment of potential threats, allowing for quick containment and minimizing damage. Once an incident is detected, a prepared organization can swiftly contain the threat, eradicate the root cause, and recover affected systems to restore normal operations. Containment strategies should isolate affected systems, while eradication focuses on removing malicious code and patching vulnerabilities.
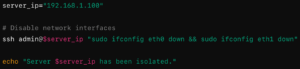
A well-prepared recovery plan ensures that systems can be restored from backups and validated for integrity. Post-incident activities, including thorough analysis and regular updates to response plans based on lessons learned, are critical for continuous improvement. Ongoing training and awareness programs for employees further strengthen the organization’s defences. Through meticulous preparation and continuous refinement of incident response plans, organizations can significantly enhance their resilience and readiness for future cyber-attacks.
Conclusion
Continuous improvement in security practices is not just beneficial but essential. Organizations must consistently evaluate and enhance their security measures to stay ahead of cyber threats. This involves regularly updating incident response plans, implementing new hardening techniques, and fostering a culture of security awareness among employees.
Now is the time for companies to take proactive steps to prepare for tomorrow’s threats. By hardening their defences and staying vigilant, organizations can significantly reduce the risk of cyber-attacks and better protect their assets. Investing in robust security measures today will pay off in the long run, ensuring that companies can withstand and quickly recover from any cyber incidents that come their way.
>>>the writer is a Cyber Incident Response and Digital Forensic Examiner at Threat Combat Ltd