“Twitter hack: 130 accounts targeted in attack” was the screaming headline on the BBC’s website on July 17, 2020.
Two days earlier, the social media site had admitted a major cyber-attack of celebrity accounts. The security breach saw accounts including those of Barack Obama, Elon Musk, Kanye West and Bill Gates tweet a Bitcoin scam to millions of followers. Several Bitcoin-related accounts began tweeting what appeared to be a simple Bitcoin scam, promising to “give back” to the community by doubling any Bitcoin sent to their address. Then, the apparent scam spread to mainstream celebrity accounts such as Kim Kardashian West and former vice-president Joe Biden and those of corporations Apple and Uber.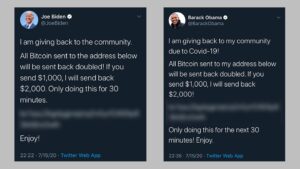
Twitter is not the only high-profile company that has been hit. Just about every other company you can think about has suffered a similar fate. The roll call of victims includes Rupert Murdock’s News Corp, Sony PlayStation Network, Government of turkey, Britain’s Serious Organized Crime Agency, and the CIA amongst others.
The story of hacking will not be complete without Anonymous; a sophisticated group of politically motivated hackers who have emerged since 2011. Anonymous are demonstrating how vulnerable companies that are charged with protecting our data are. Anonymous hacked 485 Chinese government websites, some more than once, to protest the treatment of their citizens. Among their major successful hacks are Visa, MasterCard, Amazon, PayPal, PostFinance, Bank of America, and Sony Computer Entertainment. We are at the beginning of the mighty struggle for the internet with the aged old dilemma that pits the demands of security with the desires for freedom.
Cybercrime has now become so prevalent globally that there is hardly any organization that  is yet to be hacked, and Nigeria is no exception. In fact, it is said that there two types of organizations, those that know they have been hacked and those that don’t. If in doubt, ask your customers, and they will have a bucketful of useful feedback for you.
is yet to be hacked, and Nigeria is no exception. In fact, it is said that there two types of organizations, those that know they have been hacked and those that don’t. If in doubt, ask your customers, and they will have a bucketful of useful feedback for you.
The increasing trends in cybersecurity breaches are due to the following factors; the rise of Artificial Intelligence (AI), adoption of Internet of Things (IoT) – with over 25b devices forecasted to be connected by 2025, globalisation of cybercrime, the cybersecurity skills gap that continues to grow, Increased skill levels of attackers, increased use of the Public Cloud, increasing reliance on technology and digitisation – (now fuelled by the pandemic and working from home) and attackers risk/reward imbalance amongst others.
Polls at a recent cybersecurity webinar that I facilitated was very revealing:
- 54% of respondents said they had been hacked
- 31% said their company had been hacked
- 67% considered PEOPLE the weakest link in cybersecurity – way over Process, and Technology.
And yet we spend significantly more money on products and technology, with little emphasis on mass education.
Hiring the most accomplished CISA, however, will not do very much good if there is not a deliberate policy of self-awareness of all staff, especially during this period where there is an explosion in people working from home and connecting to enterprise servers through personal systems that could more easily be compromised. Neither is buying the most expensive antivirus the magic wand. It is like having the best pizza toppings without the base bread. Or like having the best machine learning algorithm without the Big Data that the system will use for pattern detections.
Cyber-attacks can have a significant business impact including; loss of funds, theft of intellectual property, serious disruption to business, damage to reputation, loss of customer trust, huge regulatory fines, litigation costs and possible bankruptcy.
Risk mitigation against cybersecurity is most effective in its Dynamic Collaborative Form. Dynamic because it requires a shared Body of Knowledge that is consistently updated and available to all parties. Risk mitigation cannot be a competitive strategy for any organization; this notion could be quite illusory because the nature of cybercrime can be likened to an elephant. People at the side may think it is a wall, people at the trunk may think it is a snake. People at the tail may think in it is a monkey, and people at the leg may think it is a tree trunk.
As in the case of the elephant, it is only when you have curated the complete and accurate picture through which the breach can manifest that you can effectively deal with it or contain it. This is why there is a need for constant collaboration and open and transparent reporting, similar to the way that the COVID Pandemic is being collectively monitored and reported globally. This is what helped to curb the chain email fraud also known as “419” and many malicious computer viruses unleashed to take over users’ systems.
Governments and private establishments can improve the protection of critical infrastructure from cyber-attacks by following the following basic principles:
- The first rule is not to assume anything is secure.
- Second is not to assume you will not be targeted.
- Third, is to realize that modern systems have so many moving parts that you can’t really use a strategy of owning all of it, partnerships are essential.
- Nations have to build extreme levels of expertise across a wide threat surface. It’s no use protecting the databases while the CCTVs in the President’s office and residence have been compromised.
- Nations have to build cyber armies and cyber police to tackle external aggression, protect national assets and protect their citizens.
The most dangerous intruders are not the ones with guns but the ones with laptops. The terrorist killing people with bullets is “small fish” compared to the one that can make planes fall from sky or trains crash, or provoke a riot or influence an election without leaving any trace.
 Cyber-attack is the new normal. Organizations and Technology Providers can mitigate these attacks by Perpetual state of vigilance. Every internet-connected or smart device is a potential back door. From the internet-connected TV to your webcam or printer. Even if nothing is stolen from you, your resources can be hijacked to attack others. Don’t assume you have enough expertise to be in a constant state of vigilance all by yourself. Cyber products and cyber companies are also at risk.
Cyber-attack is the new normal. Organizations and Technology Providers can mitigate these attacks by Perpetual state of vigilance. Every internet-connected or smart device is a potential back door. From the internet-connected TV to your webcam or printer. Even if nothing is stolen from you, your resources can be hijacked to attack others. Don’t assume you have enough expertise to be in a constant state of vigilance all by yourself. Cyber products and cyber companies are also at risk.
If you are a transaction-oriented company then you have to be using Artificial Intelligence to watch out for fraudulent transactions. If you are a data company then you need to think of encrypting data at rest and in transit. Two-factor authentications are a must for all sensitive access. Walling off all critical systems from the net as a last means of firewall is simply not a practical solution.
Are organizations and private establishments in Nigeria doing enough to collaborate on threats? I believe that we could do more.
There should be a national Security Operations Center (SOC) and threat Database where all incidents are reported. This center should also disseminate threats and analyze incidents to help others prevent similar infiltrations. Many firms, especially banks, think it will impact their brand if they disclose vulnerabilities and attacks. The under-reporting or cover-up of breaches portends a vicious cycle of repeated unanticipated hacks because you are inadvertently empowering the hackers to cause more damage to you by not reporting and exposing them and their future hacking plans.
Working in silos is not an option, because even when you believe you have secured your fortress; how do you guard against third parties connecting to your system through Application Programing Interfaces (APIs)? Take for instance the case of the N11b breach involving a major Nigerian Bank and a Fintech company, E-Transact.
According to a report by TechNext.com, this came to light following a petition that the company developed a solution which helped Smart micro Systems to defraud the bank. Have we thoroughly investigated and comprehensively documented the nature of the beach and the vulnerabilities exploited? The demography and architype of the perpetrators? Any possible internal collaboration or any systems bugs? Answers to these question to the right quarters is invaluable in foiling future attacks. While this may not be the only major successful breach, the system is so opaque that you will struggle to find a database of cases to learn from and anticipate future attacks.
The major reasons why organizations generally do not report breaches are fear of litigation or regulatory action and loss of reputation. In tackling cybercrime, we all have to be on the same team!
According to iafrican.com, Nigeria is set to establish a Cyber Security Research Centre (CSRC) to combat cybercrime. This is in a bid to build capacity and co-ordinate incident management and contribute to knowledge generation in cybersecurity. According to reports, Nigeria is already working with Cyber Security Malaysia and the Canadian Cyber Incident Response Centre (CCIRC) on establishing the CSRC.
While these are useful initiatives, there is a need for organizations to come together to  collaborate on researching past breaches and documenting them and comprehensively reporting current breaches to learn from them in order to prevent future attacks. Private organizations such as the Risk Management Association of Nigeria (RIMAN) and the Bank Directors Association of Nigeria (BDAN) could be hardened and work closely with Government Agencies such as the National Information Technology Development Agency (NITDA) on existing and new initiatives towards combating Cybercrime.
collaborate on researching past breaches and documenting them and comprehensively reporting current breaches to learn from them in order to prevent future attacks. Private organizations such as the Risk Management Association of Nigeria (RIMAN) and the Bank Directors Association of Nigeria (BDAN) could be hardened and work closely with Government Agencies such as the National Information Technology Development Agency (NITDA) on existing and new initiatives towards combating Cybercrime.
Cybercrime and cybersecurity are real, but they are not rocket science and they are certainly no scarier than COVOD or EBOLA. If we could contain Ebola, Aids and 419 through collaboration, then surely, we can also contain cybercrime through Collaboration too; but we must be willing to take the painful steps that are necessary to safeguard ourselves and our organizations. Only then can we build the requisite trust in the system to continue to enjoy the fruits of digital transformation.
>>>the writer is the Founder of CWG Plc, the largest ICT Company on the Nigerian Stock Exchange & Entrepreneur in Residence at CBS, New York. Austin also serves on the Advisory Board of the Global Business School Network, and on the World Economic Forum Global Agenda Council on Innovation and Intrapreneurship. Austin now runs the Ausso Leadership Academy focused on Business and Entrepreneurial Mentorship.










