The protection of people, data, processes, physical assets and reputation is of pivotal importance for organizations, especially during the ongoing COVID-19 pandemic. We argue this crisis significantly increases insider threats and risks on all levels. With so many employees working from home on their own computers, laptops and mobile devices, the risk of a data breach and insider threats is increasing at an exponential rate.
Facts & Figures
According to FBI on April 20, 2020, instances of cybercrime appear to have jumped by as much as 300 percent since the beginning of the coronavirus pandemic. According to a research done by Trend Micro, the following COVID-19 related Threats were recorded for United States in the first three months.
- 907K – Total spam messages related to COVID-19
- 737K – Detected malware related to COVID-19
- 48K – Hits on malicious URLs related COVID-19
- 220x – Increase in Spam from Feb to March 2020
- 260% – Increase in malicious URL hits from Feb to March 2020
But how does the COVID-19 crisis impact insider threats and risks?
An insider threat is posed by an individual who has or had authorized access to an organisation’s network, system, or data, who, wittingly or unwittingly potentially causes harm to the organisation. The problem of insider threat, impacts organisations across all industries. Although the attack methods vary, the primary types of insider acts — theft of intellectual property, sabotage, fraud, and espionage—continue to hold true and are increasing with the expanding use and reliance on digital technology.
Vast opportunities for hackers and insiders
Malicious (nation-state) hackers thrive on chaos and confusion and the global COVID-19 crisis represents a perfect storm. For insider threats in particular, the crisis has given rise to three key conditions that have placed actors in an advantageous position.
- Exploiting additional privileges – Many companies have been forced to promptly adopt solutions allowing staff to work remotely before performing a security risk assessment and providing additional privileges and accesses to be able to continue (team) work. This allows existing malicious insiders to exploit further data sources.
- Reduced vigilance – Most organizations were not prepared for remote working or had any policies pertaining to telecommuting in place. Security awareness programs often fail to address how to work remotely. The result? An increased likelihood that untrained employees unintentionally share and leak information via insecure channels or malicious sites. In addition, the familiar surroundings and safety of one’s home can reduce the vigilance of employees handling confidential data, such as privacy sensitive data as well as business secretseven further. In turn, this exposes organizations under the jurisdiction of GDPR and other privacy regulations to considerable fines and penalties if proper handling is not assured.
- COVID-19 phishing expeditions.Phishing attacks through social engineering have been taking advantage of workers’ concerns about COVID-19 and their need to learn more about the virus and helping others in this time of need. Threat post recently highlighted how COVID-19 phishing emails evade Proofpoint and Microsoft Office 365 advanced threat protection (ATP) solutions. These emails may purport to be from the World Health Organization or other health information centers, increasing the likelihood of users clicking. Once attackers have gathered insider credentials, they can access those resources a user is permitted to use. And they will, especially if the information is interesting.
These unique circumstances of changes in working conditions increase the risk of both unintentional and malicious insider acts.
Are your employees taking your data?

When it comes to insider threats to data security, too many organizations are in denial. Not all employees will take company data, but chances are high that if you don’t put proper precautions in place, employees will put your valuable Intellectual Properties at risk, either intentionally or accidentally.
This isn’t a matter of opinion: hard facts tell the story. According to the most recent Verizon Data Breach Investigations Report, the percent of data breaches caused by insiders rose to 34% in 2018 from 28% in 2017.
With just over one-third of all data breaches caused by insiders, the threat is just too serious to ignore. Yet, although many companies understand the risk, they don’t take the threat seriously enough and those that do are unsure how to best address the challenge.
Warning signs of data theft by employees!
People and data are on the move now more than ever. Cloud solutions and collaboration tools make it easy for employees to access and share a wide range of sensitive information, such as details about the company’s customers, finances and strategy. In particular, when employees plan to leave an organisation, they sometimes use their access rights to steal intellectual property and other data they can use in their next job, or to delete content out of spite.
To mitigate these risks effectively, organisations need a clear understanding of what techniques are most likely to be exploited and which activity is a sign of an insider threat in progress. Below are some of the warning signs you need to look for:
You can spot data theft attempts in real time by watching for events such as:
- Mass file deletions or downloads from SharePoint Online
- Failed attempts to access valuable files and shares
- Logging into corporate systems at odd hours
- Repeated tries to log on to an account, which can indicate a password-guessing attack
What can organisations do to prevent/reduce insider threats?
The belief that effective perimeter security is the best way to protect data is a fallacy that is being repeatedly exposed. We must recognise the need for a data-centric security model to protect data from both internal and external threats, but what does this mean for security professionals?
To optimise security arrangements, organisations should adopt a data-centric security model that makes use of preventative, detective and reactive controls, putting in place measures that assume breaches will happen so as to create organisational resilience.
Throughout this lifecycle, insiders have access to their organisation’s information. If organisations are going to protect their data better and reduce the frequency and impact of incidents, security controls must take account of the insider threat.
As insiders are able to bypass many controls, perimeter-based solutions are not adequate to protect an organisation. Additional measures are required for each stage of the information lifecycle to ensure data is protected as it is copied, shared, reused, repurposed, backed up or archived.
Need for Information risk assessments
Information risk assessments will determine the appropriate controls for the specific threat events associated with each stage of the lifecycle that take advantage of the trust vested in insiders. But security controls can, and do, fail. More than 90% of incidents are caused by control failure, suggesting controls alone are insufficient. Incident response, recovery and governance functions all form part of the required solution.
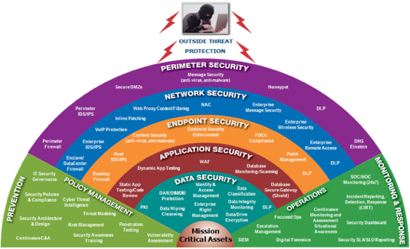
Adopt defence in depth approach (holistic approach)
Multiple types of security measures including policies, best practices, technology. As with the military definition the idea is to weaken an attack by delaying it.
In conclusion
The COVID-19 crisis will have a permanent impact on the world and the geopolitics by which it is governed, the way we do business and the way we work together. This requires a new focus on appropriate measures to conduct safe, secure and continued business in a profoundly more turbulent environment.
Many organizations have started the process of adopting holistic approach to insider risk management, but those that haven’t should not delay. COVID-19 has changed the threat landscape and the elevated insider threat it has created will be relevant for a long time. Maintaining oversight of your key risks to protect your people, assets and reputation is critical during this time. Don’t lose sight of risks when they are actually increasing. Empower employees with training and an on-guard mindset to protect digital estates from modern cyberthreats.
We welcome your feedback and suggestions.
>>>Del Aden is the Managing Partner, Delta3. As an Enterprise Architect and Information Security Consultant, Del Aden is an industry-recognized security expert with over 20 years of hands-on experience in consulting, training, public speaking, and expert witness testimony. As the Managing Partner for Delta3 International, Del now focuses on helping customers prevent security breaches, detect network intrusions, and respond to advanced threats. An astitute speaker and trainer, Del is on the cutting edge of cybersecurity research and development. For comments, contact author: [email protected] Mobile: 0202 621350 (GH) or +44 7973 623 624 (UK). Website: www.delta3.co Contact us: [email protected]
Support Information Security in Africa by sponsoring this Weekly Article and promote your Brand










