Insights are everything. In cybersecurity, insights lead to better strategies as businesses keep their online activity safe and secured both for themselves and their consumers; a key part of their business continuity plan (BCP). This article hopes to provide “quick-win” insights for Chief Information Officers (CIOs) and decision makers in investing in cybersecurity programs for their organizations.
A simple analysis of an antivirus program report (See Figure 1: Threats blocked by antivirus software for ‘Organization A’ between Nov ’19 and May ’20) revealed so many insights that could lead to actionable strategies to safeguard organizations going forward. This antivirus analysis was done on threats that were successfully blocked by an antivirus system over the course of six (6) months for an organization in Ghana. The study was conducted on 17 workstations (based on available data with false positives taken care of) between December 2019 and May 2020.
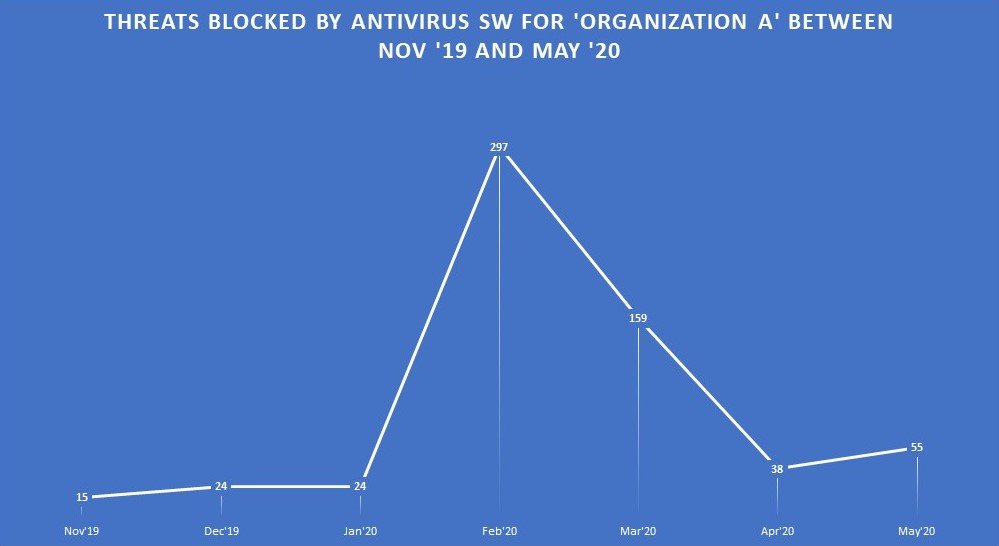 Figure 1: Threats blocked by antivirus software for ‘Organization A’ between Nov ’19 and May ’20
Figure 1: Threats blocked by antivirus software for ‘Organization A’ between Nov ’19 and May ’20
The insights revealed the following:
February and March 2020 recorded 31% more threats blocked than in the whole of 2019. This gives a subtle indication of the rise in threats due to the coronavirus pandemic [WHO reports fivefold increase in cyber attacks, urges vigilance. (2020, April 23). www.who.int] Users were either looking for coronavirus-related information within this period or downloading all kinds of applications onto their computers, taking advantage of the free internet at the office, before the work-from-home policies were implemented.
- By April 2020 however, the number of blocked threats had reduced to just 38 (76% drop), rising steadily to 55 blocks by the time of collecting the data (29th May 2020). This could be attributed to the fact that employees’ online activities had reduced during the lockdown (no “free office internet” means reduced online activity), but started rising again when work resumed gradually in May 2020.
- Other insights included:
- 346 malware detections in downloaded applications, representing 5% of all threats in the period.
- 72 trojan detections majorly from visiting unsafe websites, representing 8% of all threats in the period.
- 194 worm detections, representing 9% of all threats in the period. These were majorly from files dropped by other malware or files downloaded unknowingly by users when they visited malicious websites.
- 5 virus detections, representing 8% of all threats in the period.
- The threats that were blocked ranged from threats with a low information exposure/damage potential to very high information exposure/damage potential.
Management insights and the need for visibility
Managers with insights as simple as the above can decide on signing up to an Information Security Management System (ISMS) platform [ISO/IEC 27001 – Information security management. (2020, April 3). www.iso.org] to address employee online behavior, data and technology use. For instance, sensitizing employees on their cyber activity to ensure total awareness when in the cyberspace and regulating Universal Serial Bus (USB) device use within the organization. Apart from employees, new attack surfaces are being introduced with the adoption of artificial intelligence and automation technologies, coupled with high-speed connectivity technologies like 5G which can enable quick data exfiltration when attacked. Ever so importantly, real-time visibility into the cyberactivity on your network will provide actionable insights for immediate and further action, with the potential to minimize damage.
Real-time visibility is enabled by implementing a Security Operations Center (SOC) or signing up with a Managed Security Services Provider (MSSP).
However, before investing in visibility, it is best practice to perform a vulnerability and risk assessment of your IT environment to know what threats are already present, drawing a plan and budget to handle those, before signing up for an MSSP service for continued visibility.
A very good assessment will provide a number of recommendations that may include:
- Adopting and implementing policies (the ‘why’), standards (the ‘what’), procedures (the ‘how’) and guidelines, with emphasis on the specific industry’s cyber security standards/directives available for adoption (International Organization for Standardization -ISO, National Institute of Standards and Technology-NIST, International Electrotechnical Commission-IEC, Bank of Ghana Cyber and Information Security Directive, etc.)
- Implementing real-time visibility through building a SOC or signing up with an MSSP service provider.
- Improving Network security through network segmentation [What Is Network Segmentation? (2020, March 30). www.cisco.com].
- Ensuring secured system configurations & IT practices. Rapid 7’s “under the hoodie” project [Under the Hoodie 2019: Security Lessons Learned from 180 Pen Tests. (2019). www.rapid7.com] revealed the top 4 vulnerabilities from external assessments, as weak transport layer security (21.6%), system misconfigurations or other (17.5%), weak password policy (11.3%), and outdated software (11.3%).
While it is most ideal to invest in all the recommendations from a thorough assessment, it is practically unattainable in one go, largely due to budget constraints. This article recommends that signing up for an MSSP service for visibility is a quick win investment. I recommend opting for a company which has international experience as well as experts with a wide exposure to different kinds of attacks that have happened in the past. The MSSP should have enough threat intelligence feeds and should be well-versed in the current and future threat landscape.
Signing up for an MSSP service will remove the burden of upgrade which is transferred to the MSSP provider. Further to that, MSSPs also provide incident response in the event of an attack to ensure minimal damage and provide (in most cases) forensic analysis, to help the organization learn and prepare for future attacks. Coupled with automation capabilities, perhaps the most important benefit of signing up to an MSSP is the expertise (experienced responders, analysts and threat intelligence experts) you receive.
Conclusion
Whiles there is no guarantee of a fully protected IT infrastructure/network environment free from compromise, gaining visibility is a step in the right direction in your journey to ensuring that you have the right insights for decision-making and quick incident responses.
The author is a Digital Solutions Expert & Business Analyst | email: [email protected] | Skype: Kwadwo_2010 | LinkedIn: Kwadwo Akomea-Agyin, PMP, MRes.










